Windows 10: How to secure your applications with Exploit Protection
The component Exploit Protection, moderately obscure, ensures the framework and projects against robbery. Here is a strategy to arrange it without making an excessive number of inquiries.
With Windows Defender, Microsoft has fundamentally reinforced the assurance highlights of its working framework, including an infection identification motor, a firewall, URL separating, and that's only the tip of the iceberg. Among the slightest known devices in this bundle is the Exploit Protection, a product that gives an entire weapons store of hostile to robbery shields with odd names, for example, "control stream assurance", "information execution aversion" or " to drive the randomization of pictures ".
Behind these dark terms are concealed capacities whose intention is to upset interruption methods utilized by privateers. They have been produced logically since 2009 as a major aspect of the EMET (Enhanced Mitigation Experience Toolkit), a free programming made by Microsoft and recently expected for framework overseers. With Windows 10, the distributer has chosen to incorporate every one of these capacities specifically into its working framework and make them open to all.
Adventure Protection frames an extra line of guard notwithstanding the firewall and infection recognition motor. To design it, go to "Windows Settings - > Update and Security - > Windows Security - > Application and Browser Control". At that point look down to the base of the page and tap on "Adventure Protection Settings".
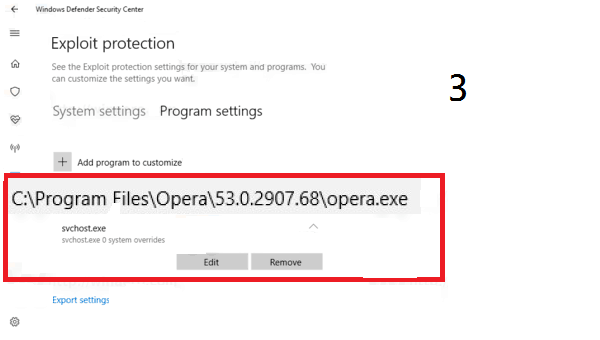
The window that opens at that point offers two arrangement boards: "Framework Settings" and "Program Settings". We don't prescribe contacting the initial ones which are, generally, officially initiated as a matter of course. Then again, it is conceivable to fortify the settings concerning the applications.
Of course, the "Application Settings" sheet as of now records some Microsoft programming. In any case, it is conceivable to add others to submit to hostile to theft procedures Exploit Protection. The perfect path is to include the applications you utilize frequently and which appear to be essential to you: your Internet program, your saving money application, your content tool, your PDF watcher, and so forth.
To include an application, just tap on "Add a program to tweak" and pick the alternative "Pick the correct record get to way". You would then be able to choose the executable document of the application being referred to by exploring in the record tree. The executables are situated in the "C: \ Program Files" and "C: \ Programs" registries. For instance, we picked the Opera program. When your application is included, select it and press "Edit".
You are then gone up against with a rundown of around twenty security choices with outlandish names, for example, "Discretionary code insurance", "Square pictures of low trustworthiness", "Assurance of control stream". In this article, we won't clarify the significance of these choices, which depend on exceptionally specialized ideas. Some have been empowered as a matter of course by the framework. Others can be by hand.
The issue is that they can crash the application on the off chance that they are excessively defensive. This is clearly the situation of the "Code Integrity Protection" choice, which, when enacted, just permits the dispatch of uses made by Microsoft or from the Microsoft Store. Likewise, the choice "Don't permit youngster forms" is an awful thought with regards to an internet browser on the grounds that the route tabs that are opened are simply tyke forms.
To shield its application however much as could be expected, we prescribe experiencing it bit by bit, enacting the choices one by one and checking each time that the product works effectively. On account of Opera, we figured out how to initiate nine extra assurance alternatives out of the three that were at that point there. It takes a little tolerance, yet we arrive. Or more all it's anything but a major deterrent for the individuals who truly need to profit by better security.



Post a Comment